How Digital Companies Anticipate Data Security and Privacy Issues
Discussion with AVP Information Security Blibli Ricky Setiadi
Data security and privacy has become an important focus in recent times. Multiple platforms in Indonesia have issues in this area impacting tens of millions of user data. Of course, this is bad news for the digital ecosystem that is developing, especially services that have recently leaked tend to be from large technology companies – in terms of business scale and user coverage.
Aspects of data security and privacy (ideally) are components that must exist in a digital product development process. Discussions about anticipating steps to this issue have become interesting – especially for the startup ecosystem in Indonesia, where most of their products are digital and involve users' personal data.
To comment on this, DailySocial opportunity to talk with AVP Information Security Blibli Ricky Setiadi.

Here are the results of our interview:
DailySocial (DS): The issue of data breach is actually not new in Indonesia, but it becomes a byword when it involves B2C/C2C platforms with large user bases. From Pak Ricky's experience as a practitioner in the field of cyber security, can you explain most of the incidents caused by what factors?
Ricky Setiadi (RS): The risk of the threat of data leakage on digital platforms always in a very high range. If using a risk matrix, data leakage can be categorized into high to critical. This value will be obtained from a combination of the impact of the frequency (how often it occurs) and the scale (how big the impact) of the data leak event.
The scope of data leaks on a large scale is usually carried out because there are gaps or gaps in the data vulnerability of the system created by an organization. Cracks are caused by various factors, but in general they fall into three major groups, namely: People, Processand Technology.
(1) People -- Data leak occurs because human error or human negligence, it can be from the developer's or user's side. Users sometimes trust developers too much. Even though data security is a shared responsibility, so that involvement from the user's side is still needed. Some basic security implementations that can be done from the user's side include the use of Password good (character combination Password, use Password different for each platform, and replace it periodically). Users also need to have awareness or knowledge of threats social engineering (like Phishing).
It is undeniable that many incidents also occurred due to errors in the development process or maintenance a digital product. For example, the developer did not implement encryption for the use of variables username and Password, and storage private key unsafe, or there is use default account for each system used. Another example is negligence in doing maintenance such as developers using expired digital certificates, use unprotected, to negligence in doing system design (don't heed the rules standard practice based on risk in the division of systems that can be accessed publicly and systems that can only be accessed by internal).
(2) Process -- Exploitation of business processes. Sometimes criminals take advantage of errors or omissions in an organization's processes (logic flaw exploitation). Paradigm that security is a shield or as the last protection of a product, can be one of the main factors for data leakage. At Blibli, we always try to test our products from the early stages of their development to avoid attacks at every stage. The absence of testing the system in the development process is also one of the errors that have an impact on the occurrence of data leaks.
Developers should also remember to apply protection to the hardware. Some cases of data leaks also occur due to the exploitation of hardware containing customer data, for example such as security server or hard drive which stores data offline.
Technology – Criminals find loopholes in developer technology. Technology is the result of a product development of human logic. Through a different (reverse) logical approach, many criminals take advantage of this loophole to later serve as an agent pintu in retrieving data from an organization. As one example is the adoption of the TLS 1.0 data security protocol, in 1999 this technology was widely used to support transaction services online. But over time, a security hole was found in TLS 1.0 that allowed it to happen “Man in the Middle” attack. With this loophole, perpetrators can do intercept against transactions made by the victim or the target.
If you look at the three components above and based on development data incident reports issued by various studies (one of which is cyware.com), the current trend of attacks and data leaks occurs due to many factors People through social engineering. Social engineering as Phishing, making it easier for the perpetrator to trick the target. At the same time, Phishing also used as the main media in spreading malware. This combination is thenMaintain by the perpetrator for a new attack commonly referred to as Advanced Persistent Threat (APT) attack. With APT attacks, actors then develop and exploit data which can then be commercialized/sold.
To that end, education about social engineering to all parties involved in a business process is one of the priorities to maintain data security, especially customer data. Blibli, as a developer and provider of digital services, actively educates all stakeholder up to the customers. Education and information dissemination are carried out regularly so that Blibli can carry out comprehensive security controls.
DS:From the developer's point of view, what are the things that need attention early on so that the system always accommodates data security and customer privacy? What factors are closely related to the security and privacy of user data?
RS:Data and information security is a shared responsibility. Customers must be observant to limit the information provided to digital service providers and understand the risks if the information requested is too sensitive and not related to the service.
This limited understanding of data security is what makes team involvement Security at each phase of development is very important. Team Security can minimize the occurrence of interference with customer data, especially data that is privacy or secret (personally identifiable information or PII). Security is not only limited to technical safety factors when digital products are ready to be made, but the application of security must even be carried out when the product is designed according to standards. best practice.
Here are some security factors that need to be considered, especially when processing personal data, namely:
- Government regulations. Ensure that all aspects of regulations issued by the local government have been serve as one of the main references in the process of retrieval, processing, delivery, and storage of customer data. This is important because each region will have different laws and regulations.
- Security policy. Every developer today must have an umbrella that is used in data security, especially customer data. This umbrella is usually set up in a Privacy Policy. In making this policy, make sure it is made in the simplest possible format and in easy-to-understand language without forgetting the aspects of transparency and security.
- Risk measurement. Another consideration in safeguarding and securing at the time of application development is through the approach to measurement for each risk. There are several benefits that can be taken when a risk assessment is carried out. In addition to identifying any potential threats that will occur, the use of effective controls can also reduce the cost burden in the mitigation process, considering that each risk will have different weights and values as well as controls. Of course, in measuring this risk, every organization must apply or have acceptance criteria (acceptance level) and the response plan (risk treatment plan parameters).
- PII data collection. In the development of a platform will definitely use at least one of the personal data. For example, data is full name, email address, or telephone number. Developers must take into account and carefully consider the extent to which the product design will process the data. For example, in the registration process, will the platform we develop require complete data such as the name of the birth mother, even though the platform being developed is not for banking services. Another example, do we need data in the form of an identity card or? Credit Card at the time of developing a promo feature. Or most often found in product development for smartphone, sometimes developers don't really pay attention to the needs of their applications, so there are some applications that default can access contact, gallery, camera, and so on. Make sure that the use of personal data is carried out according to the needs and when using the data it is ensured that we have proper controls for each data collected.
- Security features and processes. Nowadays security features are one of the factors that customers and potential customers will consider. The use of encryption (https in web mode or other encryption in data transmission) is one of the security features that can help in the security of customer data. In addition to features two factor authentication or recovery methods the other is another development approach that can be used as a customer attraction in data security.
In addition, in the internal process, make sure there are strict rules in granting access rights to every user stakeholder which is involved. Segregation of duties or segregation of duties is an approach to preventing internal threats. Data classification is another approach that can be done in internal business processes to prevent PII data from being exposed.
DS: During this pandemic, the online groceries platform suddenly surged in transactions. So startups need to scale-up technology from various aspects. According to Mr. Ricky, during the scale-up period, what kind of investments do businesses need to make to support system security?
RS:For us, one of the most important investments is in People and Process. In the perspective of information security, basically every system and technology is a business support tool which always contains vulnerabilities. Investing in People and Process will change the mindset and culture of the business. These two investments are what we are trying to implement at Blibli.
Changes in mindset or mindset It is educational in and out. As previously explained, organizations must also continue to inform that the security of customer data and information is a shared responsibility with a scope that is in accordance with their respective portions.
Another priority is a change in the culture of risk. Culture in a business starts from the process of implementation, adoption, to technology acquisition. If this process is carried out effectively and efficiently, the company can lower its risk profile and implement controls on the organization. Organizations can also accelerate business development because they have been able to determine the right security controls from surface attacks at the time of doing scale-up.
DS: When doing development, sometimes engineers encounter doubts. On the one hand, apps should be designed to be as smooth and fast as possible, with a very simple UX. On the other hand, the safety factor must be a concern. Causing some developers to ignore the option of adding additional security in the system. How did Mr. Ricky respond to the situation?
RS: This problem is a classic problem between the development team and the security. Some startups still use conventional concepts in doing business balancing or balancing during application development. So this classic problem always occurs and repeats itself. In dealing with this, we can actually adopt an approach Shift Left. The following is an explanation of the conventional approach and Shift Left.
Conventional:
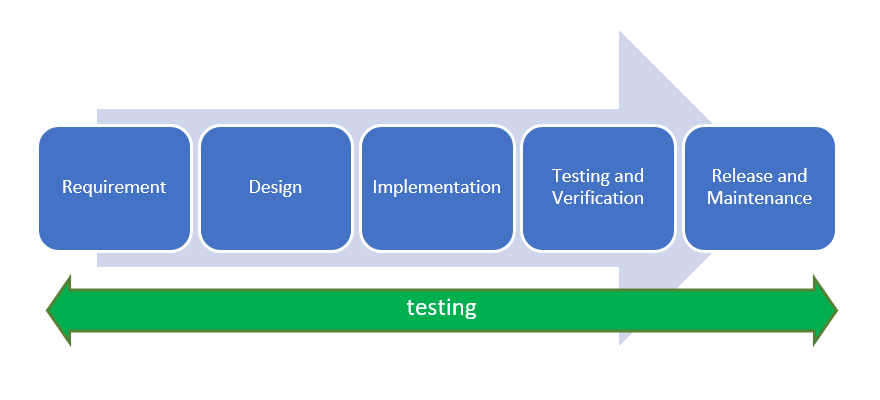
If you look back a few years, the process of developing an application will always write down all requests at the beginning of development. Process testing, including security testing, will be performed at the end of development. On the one hand, these stages will result in a mature application, but on the other hand, it will have a fairly serious impact at the time of discovery. defect result testing which are numerous and quite critical. The process of improving the results of testing will require additional costs both for design and implementation.
This method is very ineffective to be applied by organizations startup who always rely on the number release fast. Adopt a more approach agile and shift left can be done for every organization startup in producing products quickly without leaving the safety aspect.
Shift Left:
Conventional methods apply testing only in the final stage (Testing and Verification). Approach Shift Left implementing the testing process starting from the initial phase, namely "Requirements". In this phase, Requirement will not only involve customer needs in terms of products, business, and user experience, but also includes a security element as a parameter. Blibli has also applied this method in its digital product development process.
Shift left will form a paradigm for testing all aspects (test everything), tests performed at any time (test every time), earlier testing (test earlier), continuous testing (continuous test), and involving the examiner at every stage. Development team and security can work together to take preventive action rather than detective.
We have applied these methods and approaches at Blibli before we launched IT products. With this adoption, the detection process against bugs or defect to be faster, increase effectiveness in terms of development time and costs, as well as improve the ease and quality of products/applications.
DS: According to Mr. Ricky, what is the urgency to certify the system, related to data security and privacy? What certifications are recommended to follow?
RS:Certification will be a competitive advantage. Because through certification, an organization has demonstrated higher performance capabilities and is in accordance with standards. In addition, certification is also a comparative advantages of an organization. Business processes will adjust to standards so that they are able to produce more quality products that are effective and efficient and are able to carry out risk management.
There are many certifications that can be applied to the organizational level in the world of information security or cybersecurity. This goes back again to the interests and business domains of the organization. Blibli, for example, has received the globally recognized ISO/IEC 27001 2013 certification for managing information security systems. Ecommerce is a business that processes customer data, so it is important if a similar business undertakes this certification.
The certification process also needs to be carried out by individuals who carry out the security implementation process. Professionals who carry out the security process will always be an added value for the company in running its business. There are many information security certifications for individual levels such as:
- Managerial: CISSP, CCISO, CISM, CIPP, CIPM, CRISC, CGEIT, EISM
- Technical: OSCP, OSCE, OSEE, OSWE, CEH, CSSLP, Security+ CHFI, ECIH, LPT Master, ECSA Master, CREST
- Audit: CISA, ISO 2700 Lead Auditor, ISO2700 Internal Auditor
DS: In the technical team of a digital startup, ideally what should the security team consist of?
RS:Digital startups will always process data in digital form. The focus of an organization's security must go further, not only on data security alone, but much larger in the results of processing the data – usually known as information.
Technical team needs in general only need three teams, namely Yellow (architect), red (attacker) and Blue (defend).
- Yellow: When developing an application, architecture review will always be carried out both in terms of applications, infrastructure, and security. Team Security Architect will do review to architecture from applications based on functions, objectives, test plans, as well as monitoring of technical risks through the process threat modeling.
- Red: Apart from the team Yellow, an app needs to be tested internally before releasing it to the public. This test will be carried out by the team Red. The main function of this team is to simulate attacks on applications, platform, and infrastructure. The scenarios are not only limited to security tests, but also carry out various simulations hacking and social engineering as part of the tests performed.
- Blue: In addition to simulating attacks, it is used as a method for securing applications or platform, another method needed is a defensive method. Team Blue will be responsible for the implementation of scenarios and control of defense from attacks by cybercriminals or attack simulations from the Team Red like implementation web application firewall, firewall, logging, SIEM, incident handling, and a number of other defensive measures.
In its development, the three teams will form an additional team as a result of a mixture of these three colors. Blibli also applies this mix to ensure the IT team can operate optimally. The three additional teams are:
- Green Team (a combination of Blue with Yellow): This team will make a lot of improvements from security automation and queues written by developer (program).
- Orange Team (a combination of Yellow with Red): This team will help Team Yellow to increase capacity on security in the form of awareness or security technical education.
- Purple Team (a combination of Red and Blue): This team is a balancing team to increase Team capacity Red in carrying out offensive or defensive methods as well as evaluating and improving the Team Blue in defense.
DS: As a case study, how does Blibli implement data security and privacy standards? What features are provided to anticipate system failures from the consumer side and from the platform side?
RS: Blibli is committed to prioritizing customer satisfaction. One way is to ensure that the security of customer data is protected and properly managed.
Customer data security is subset or part of the information security control process, so that in practice we implement three control methods which include:
- Preventive: We control with this preventive approach by changing the culture of the information security paradigm. Some of the activities we carry out include campaigns that enhance awareness customers for data security, implement access controls and technology as needed stakeholder, as well as working with official external parties such as the National Cyber and Crypto Agency, the Information Security community to improve broader security.
- Detective: In this process, more emphasis is placed on the detection aspect in the hope that there will be improvements to improve information security and see the level of effectiveness of the controls we have. Analysis log, security testing, and periodic reports are detection measures that we carry out.
- Corrective: This control aims to improve the condition of the security level when an incident occurs. Team building Computer Incident Response Team (CIRT) and Cyber Security Incident Response Team (CSIRT), as well as the incident management process is one of the methods implemented by Blibli.
We admit that at this time the crime in the cyber world is increasing day by day both in quality and quantity. In terms of security we implement many security controls both from the customer side and our platform. The following are some points that we have developed in order to maintain data security and transaction convenience.
(1) Security of the e-commerce system.
100% Usage secure communications for publicly accessible services. In addition to making it easier for customers to shop, it also ensures that all transaction services run safely.
Implementation Bot Detection System (BDS) to detect transactions carried out by muzzle. We take this action to ensure that real customers can enjoy limited promotions (flash sales, voucher codes, etc.), not bots set up to perform exploits.
Operate Secure Software Development Lifecycle (SDLC). With adoption shift left, Blibli has implemented a secure SDLC process so that we can anticipate vulnerabilities that may occur in the application.
Implementation Security Operations Center (SOC) so that we can detect traffic which is a potential threat. In addition, with this SOC, Blibli can maintain the security of the company's digital environment from unauthorized parties so that they cannot access Customer Data.
Application and product development always prioritizes risk management aspects, where every risk will be controlled through appropriate controls.
(2) Customer protection.
Blibli added a feature Phone Number Verification and Email Recovery as one of the controls to protect and improve the security of customer accounts.
In the face of the threat of action fraud, we implement features 3D Secure for credit card payments and send OTP to customers when transacting with Blipay and BCA OneKlik.
Operate phishing site detection, a feature that makes it easy for Blibli customers in protection against trials Phishing.
end-to-end encryption for all features containing critical customer information such as Password, credit card, and other sensitive information.
More Coverage:
DS: As a worst case scenario, when the system encounters a data breach issue, what should the company do -- from the development team, communication team to customers, etc.?
RS: An organization must as early as possible prepare a worst-case scenario of an attack, including data leak scenarios. Prevention and response to data leakage must involve all parties from the IT, Security, communication, legal, and management teams.
Every organization must at least have standard procedures in preparation for handling incidents. Every incident that occurs does not have to be informed to the customer. The company must also categorize the incidents that occur (whether the incident is included in the activity category? malicious code, abnormal access use, trial spear phishing or other incidents that cause data to be exposed).
In addition to the categories above, the team incident action must analyze the impact of the incident. The use of a matrix derived from the risk matrix will help the team perform calculations more precisely and quickly. This analysis should also be supported by a validation and classification process of the incident. Is this incident really valid or just limited false positive, whether this incident had an impact according to the first report, as well as what data or systems were affected by this incident.
After conducting the analysis and classification, the next step is to determine the priority of both the type of incident and control measures for temporary repairs so that these incidents do not have a bigger impact. The initial investigation process by conducting analysis, validation, classification, and prioritization is usually known as Incident Triage. Incident Triage This must be done carefully and carefully, considering that this will be the main input for determining the next step.
If in phase incident triage results in the conclusion that the incident occurred, the notification process must be immediately given to every component of the organization involved. This quick notification should involve:
- Legal team to see from the regulatory and legal aspects that apply.
- The IT team to immediately coordinate in carrying out the initial handling of incidents that occur, including the team Infrastructure and developer to make repairs as soon as possible.
- Management representatives to provide an updated report on the status of the incident and request advice, recommendations and direction for decisions.
- Communications Team to provide an official statement (either reactively or proactively) to the public regarding the current state of the incident and whether this incident is valid or invalid.
Along with the notification process, the incident handling team must immediately run the process containment. The function of this process is to stop the rate of impact of the incident from spreading to other assets and systems. Other destinations containment is to reduce losses from the greater impact of the incident.
The incident response team must also be able to collect evidence from each of these incidents. Collecting this evidence is an important part of reporting and defining the process forensic of the incident. Results forensic it will describe detailed information from the incident such as:
- Attack method.
- The type of vulnerability used to perform the exploit.
- Security controls capable of withstanding attacks.
- The type of application or system used as dormant hosts or the attacker's access point and detailed information.
After finding the core of the problem, the incident management team immediately makes corrections to programming errors or errors patching to a number of vulnerabilities that were found and used as entry points for the incident. In incident handling, do patching This is commonly referred to as the eradication process or eradication process. Some other examples of this process are replacing malfunctioning devices, changing the configuration of both infrastructure devices, security nor queues from the developer, as well as doing improvement (installation) new to improve security.
The next step that must be taken by the handling team is to restore systems, services, and data affected by the incident. The handling team must be able to ensure that all services return to normal.
The response team must make a complete report on the incident and report it to the relevant parties. In addition to company management, the team can report it to the government if the incident falls into the critical category and relates to customers. When providing information to stakeholder, there are at least a few points that must be done or delivered:
- Communicate this incident in simple language to stakeholder right.
- Providing transparent information, including information about the involvement of all parties in planning incident preparation is one of the best approaches. Also inform that this incident is beyond the control of the organization, considering that the organization has carried out a series of preventive activities.
- Provide fair and accurate information regarding the impact of the incident. This includes information about
- What happens to the data, for example, even though the data is exposed, it is still protected by encryption.
- Steps or actions that must be taken by customers if the handling process is still in the investigation or repair stage, such as changing passwords for all digital accounts and checking balances (for financial platforms) regularly
Take action (incident response) against data leakage is a critical action that must be taken immediately. However, preventive action is the main key in reacting and responding to the data leak.
DS: Finally, maybe there are books, online courses or other learning resources that Mr. Ricky feels can be learned by startup activists regarding methodologies, concepts, to data security and privacy practices?
RS:Currently, there are many platforms that can be used to increase capacity in information security for both startup businesses and individuals. Good by nature free, freemium nor premium good from the side managers as well as from a technical point of view. Platform what we usually use is O'reilly, udemy, cyber.it, hackerone, hackthebox, hacking-lab, pwnable, coursera, open security training, Heimdal Security, san cyberaces, owasp, openSAMM project and many more some community platforms which can be used.
At Blibli, we always increase the capacity of the IT team, one of which is to educate on product development through: secure coding training, seminars, and internal sharing sessions periodically. We also invite IT colleagues at Blibli to join the IT community. The function of employee participation in the community is to expand network and get Update on current issues, both domestically and abroad.
Sign up for our
newsletter